Connect to secured networks via VPN
Codesphere provides a convenient way to work with private networks from our workspaces. Learn how it works in this doc article.
Virtual private networks (VPNs) are a popular way to secure communication to and from restricted networks. Per default most internal company networks are secured with a firewall that prevents all incoming and sometimes outgoing traffic through public internet connections, a VPN tunnel offers a convenient way to still enable communication with the outside world. All traffic running through a VPN is encrypted between the end device and the origin and runs through so-called tunnels. Codesphere provides a convenient way to configure such a VPN connection from your workspaces to any of your company’s internal networks. Currently supported network configurations are Palo Alto Network firewall encryption standards, if additional standards are needed feel free to reach out.
This enables your applications to work with restricted on-premise databases, internal APIs and more.
Working with private networks in Codesphere
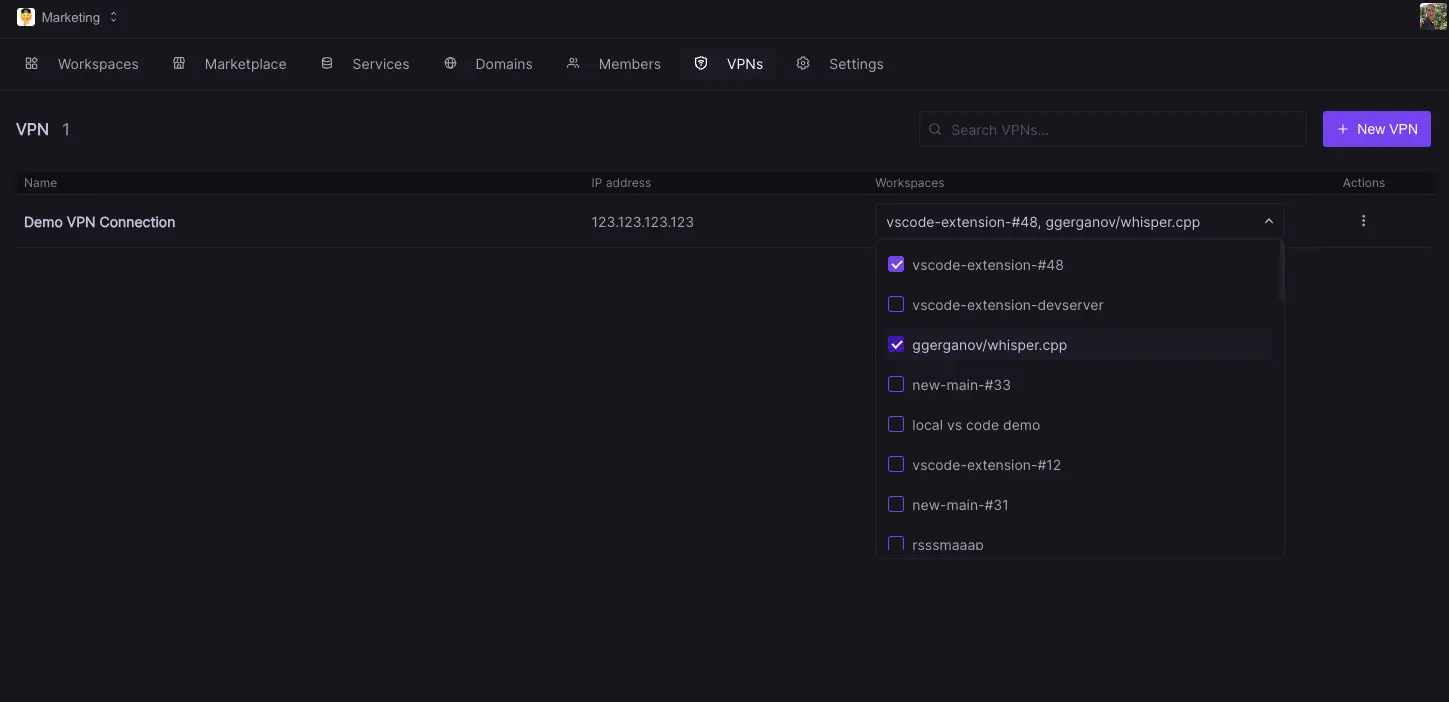
In Codesphere VPN connection are defined on a team level and can then be associated to any number of workspaces in that team. To set up such a connection head to VPNs in the main navigation (available to team admins).
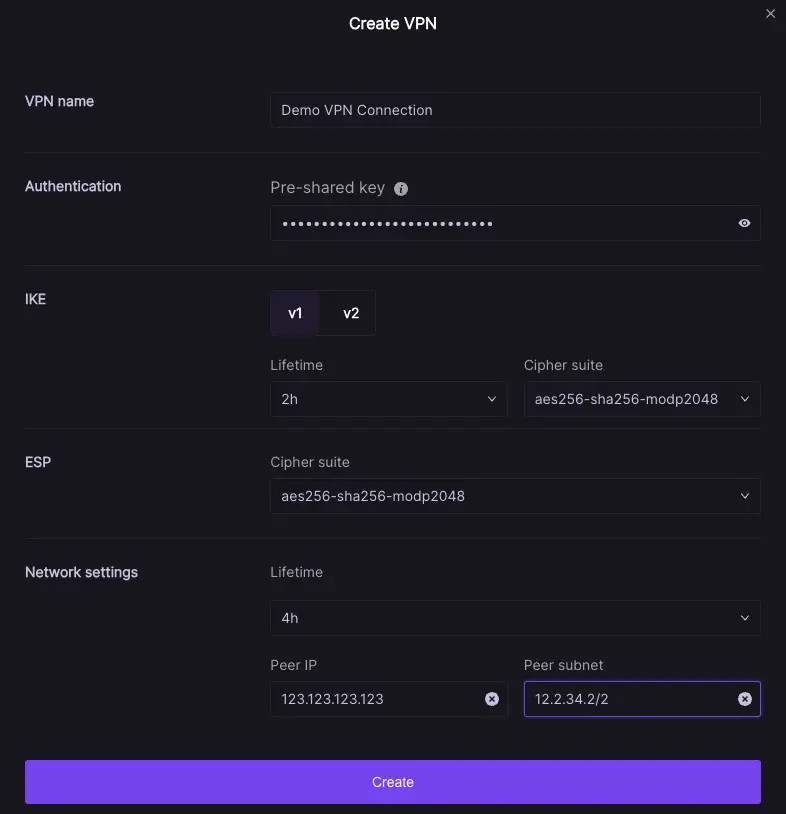
Click the create VPN button to open the configuration modal. You will need the following items to open a connection:
- A unique name for this connection.
- Pre-shared key (your networking team can configure these on a firewall level)
- Lifetime values for connection attempts.
- Cipher suites used by your firewall.
- Target IP address and private subnet (pointing towards the internal resource your application needs)
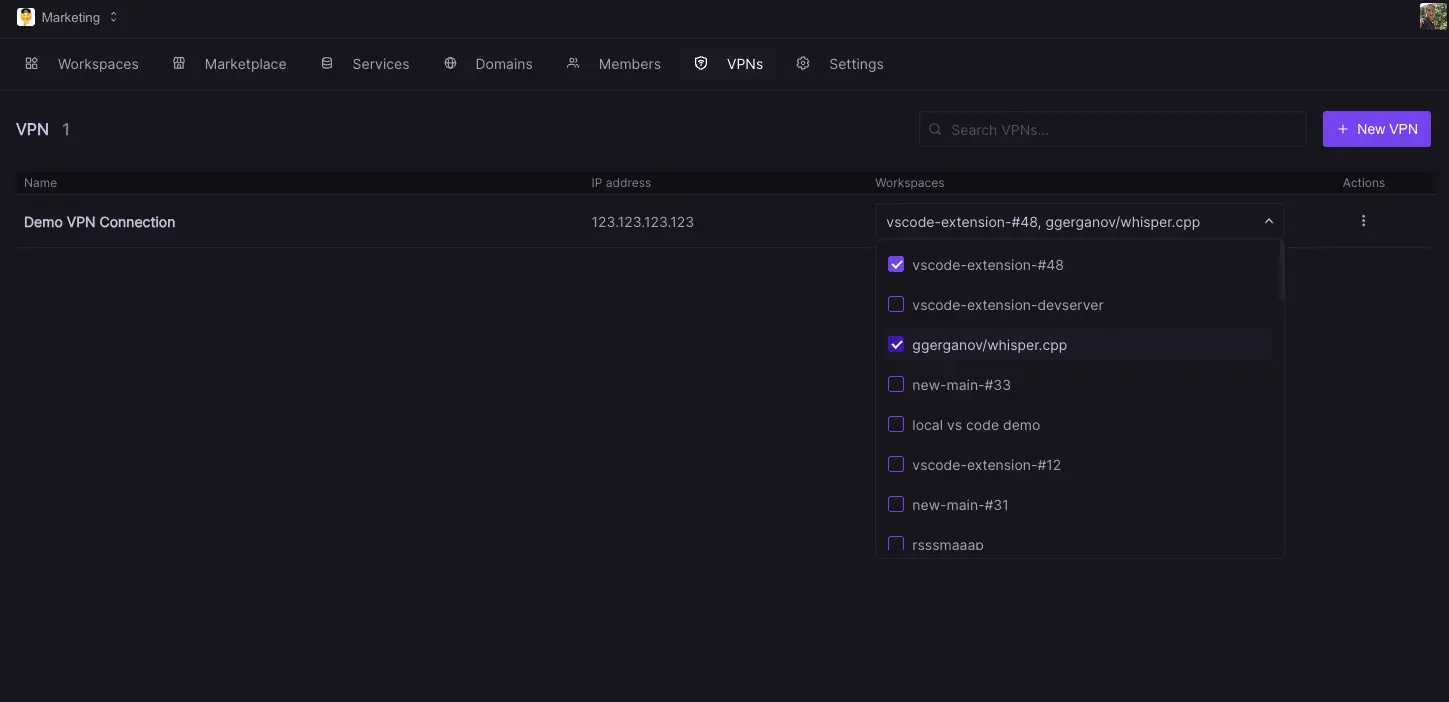
Once the connection is created it will appear in the list of available connections. You can now connect each VPN config to any number of workspaces via the dropdown. Note while a connection can be used by multiple workspaces each workspace can only connect to one single VPN. If you want to change a workspaces VPN connection you will need to disconnect the previous one first. Please also note that changing a VPNs settings will cause the VPN service of all connected workspaces to restart.
Working with VPN connections in preview deployments
You can also associate preview deployments to existing VPN connections via our CI integrations for GitHub, Bitbucket and GitLab by referencing the VPN connection name in the deploy yaml. This enables you to comfortably work with private networks for your development environments.
Bitbucket syntax:
image: atlassian/default-image:3
pipelines:
pull-requests:
'**':
- step:
deployment: Test
script:
- pipe: docker://ghcr.io/codesphere-cloud/codesphere-monorepo/integrations/bitbucket-ci:latest
variables:
ACCESS_TOKEN: $ACCESS_TOKEN
EMAIL: $CODESPHERE_EMAIL
PASSWORD: $CODESPHERE_PASSWORD
TEAM: My Team
PLAN: Micro
VPN_CONFIG: vpnConfigName
ENV: |
testing=abcGitHub syntax:
on:
workflow_dispatch:
# open, reopen and synchronize will deploy a workspace for the current commit.
# If a workspce is already deployed, that workspace is updated to the newest version.
#
# closed: Workspace will be deleted
pull_request:
types:
- closed
- opened
- reopened
- synchronize
permissions:
contents: read
pull-requests: read
deployments: write
jobs:
deploy:
# prevent multiple workspaces to be created for the same branch
concurrency: codesphere
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v3
- name: Deploy
uses: codesphere-cloud/gh-action-deploy@main
env:
GITHUB_TOKEN: ${{secrets.GITHUB_TOKEN}}
with:
email: ${{ secrets.CODESPHERE_EMAIL }}
password: ${{ secrets.CODESPHERE_PASSWORD }}
team: 'My Team' # Change this to your team
plan: 'Boost' # Select the plan for your app (Micro, Boost or Pro)
onDemand: 'true' # Set this to true for on demand
vpnConfig: 'vpnConfigName'
env: |
MY_ENV=test
MY_SECRET=${{ secrets.MY_SECRET }} Gitlab syntax:
workflow:
rules:
- if: $CI_PIPELINE_SOURCE == 'merge_request_event'
stages:
- deploy
codesphere-deploy:
image: ghcr.io/codesphere-cloud/codesphere-monorepo/integrations/gitlab-ci:latest
stage: deploy
script:
- /app/server
variables:
ACCESS_TOKEN: $CI_ACCESS_TOKEN
EMAIL: $CODESPHERE_EMAIL
PASSWORD: $CODESPHERE_PASSWORD
TEAM: 'Demo'
PLAN: 'Micro'
ON_DEMAND: 'false'
VPN_CONFIG: 'vpnConfigName'
environment:
name: 'Codesphere Preview MR_$CI_MERGE_REQUEST_IID'
on_stop: codesphere-teardown
codesphere-teardown:
when: manual
image: ghcr.io/codesphere-cloud/codesphere-monorepo/integrations/gitlab-ci:latest
stage: deploy
script:
- /app/server
variables:
ACCESS_TOKEN: $CI_ACCESS_TOKEN
EMAIL: $CODESPHERE_EMAIL
PASSWORD: $CODESPHERE_PASSWORD
TEAM: 'Demo'
environment:
name: 'Codesphere Preview MR_$CI_MERGE_REQUEST_IID'
action: stop